Security Logs
Use the Security Logs function to monitor user activity that could appear unusual or suspicious.
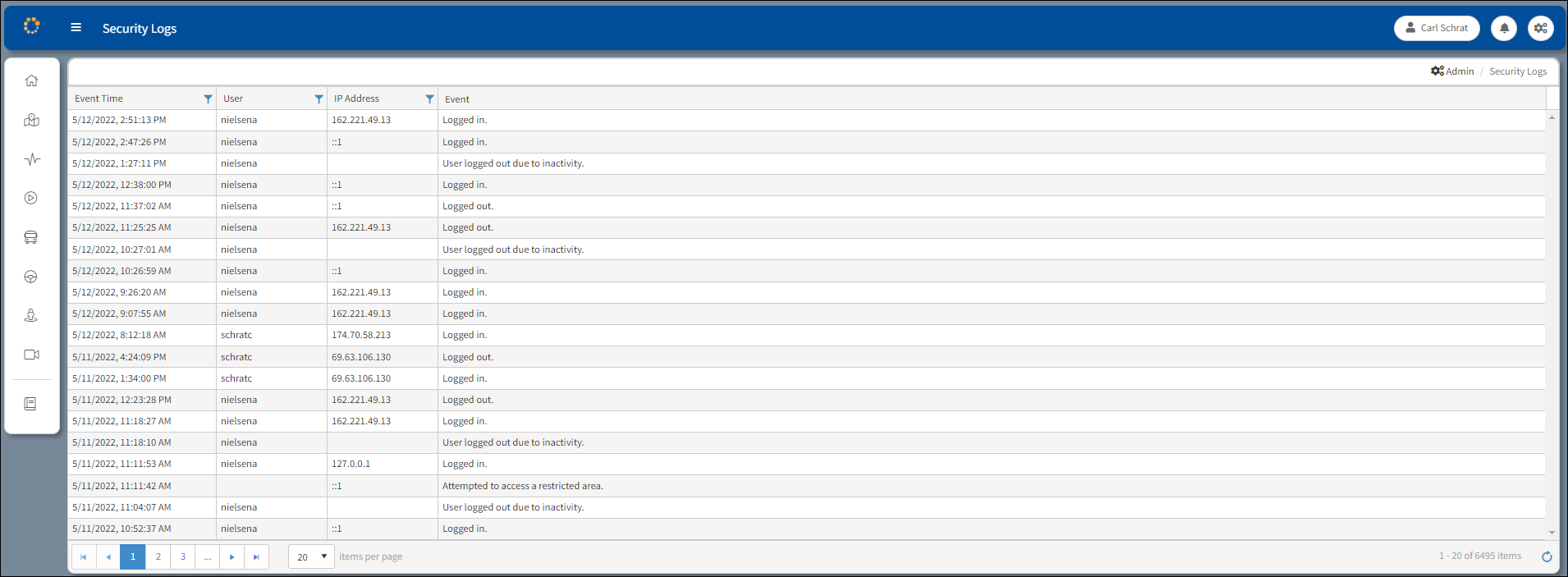
Security Logs Window
Event Time – Date and time of the event
User – Name of the user with ARMOR access
IP Address – Users' Internet Protocol Address
Event – Listed below are the types of activity that are logged in the Event column of the Security Logs window:
•Initiated password reset
•Finalized resetting password
•First logged in
•Changed password through profile
•Edited their profile
•Accepted sharing anonymous data
•Rejected sharing anonymous data
•Reset all authentications
•Logged in
•Entered an invalid password
•User is locked caused by too many failed attempts
•Logged in (via stored cookie)
•Logged out
•Added a trusted device
•Failed password challenge
•Attempted to access a restricted area
•User logged out due to inactivity
Filtering
The Event Time, User, and IP Address columns have the capability to allow filtering![]() to enable a closer review of a specific event or to examine a more narrow category of vehicle details. Refer to the Sorting and Filtering section under Introduction for information about using filters.
to enable a closer review of a specific event or to examine a more narrow category of vehicle details. Refer to the Sorting and Filtering section under Introduction for information about using filters.
